Internet Nomad Password Manager
Internet Nomad Login
During my final year of university, I developed a security-related product that encompassed various aspects of project management. This entailed conducting risk assessment, allocating resources, implementing a development methodology, and more.
Features
- You can choose your own encryption: AES[^AES] or Blowfish[^Blowfish] ciphers with PBKDF2[^PBKDF2] or Argon2[^Argon2] key derivation functions[^KDF]
- Strongest security that adapts to your hardware and patience:
- The program adapts the number of rounds to the time needed to unlock based on a benchmark
- The program can adapt to the amount of RAM available (Argon2[^Argon2] specific)
- Separate identities are available
- Shared recovery method
- Paper recovery method
- Password Generator
- Theming Support
Encryption and Data Security
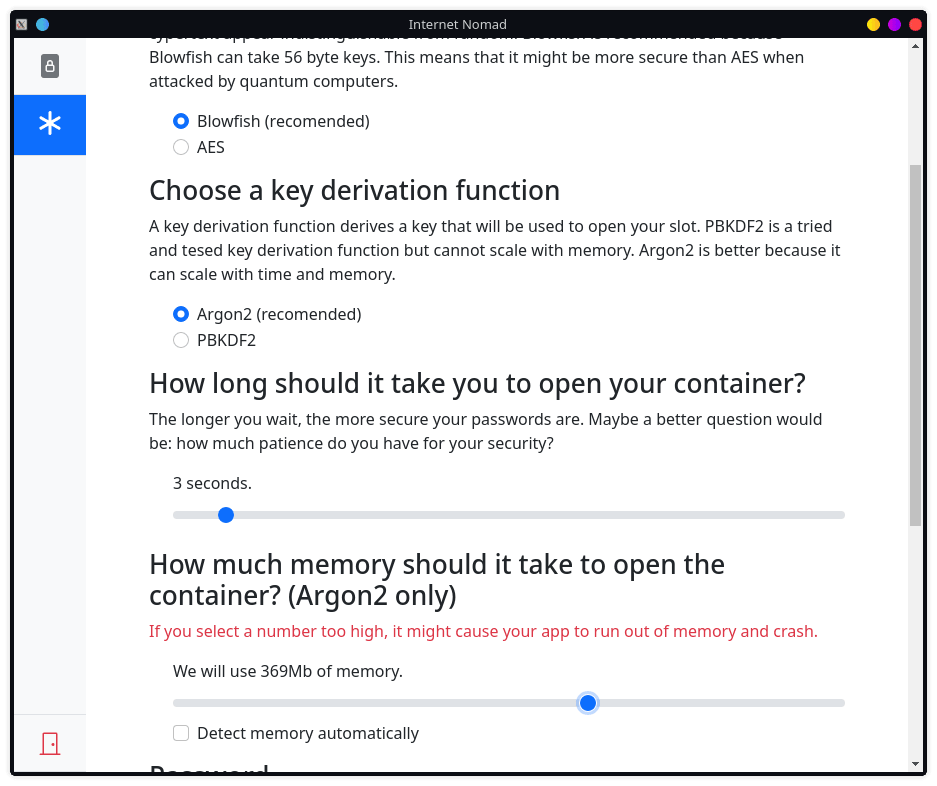
The user can choose their encryption in the password manager. The user has a choice of Blowfish[^Blowfish] or AES[^AES] as the encryption method[^ENC], and PBKDF2[^PBKDF2] and Argon2[^Argon2] as key derivation function[^KDF].
Once the user has selected the appropriate encryption settings, they can fine tune the amount of memory that the program should use and the amount of time the program should take to open one password. Multiple passwords can be added to open the password manager. This is done by encrypting and keeping a copy of the master key in each slot. This removes the need to share the same password. It also makes this password manager secure.
Shared Recovery
It's highly possible that a hypothetical adversary attempting to break the encryption on your password manager might not allow you to simply walk away. They may even become hostile, potentially leading to dangerous outcomes for the user, leaving potentially important data forever encrypted. To alleviate this, the password manager lets you set up a shared recovery scheme before such a situation arises. This scheme allows trusted individuals to unlock and access the password manager's contents. There's no way of knowing how many of these recovery schemes exist, so if done properly the adversary also wouldn't know who these trusted individuals are. A shared recovery scheme creates a number of pieces given an opening threshold, from which the master key can be derived. The number of pieces and the threshold can be set independent of each other (Adi Shamir, 1979)[^1].
Alternatively, if the user prefers, they can use a different backup method that doesn't involve the shared recovery scheme - perhaps by entrusting a single entity with a backup master key and storing the key in a secure location.
Identities
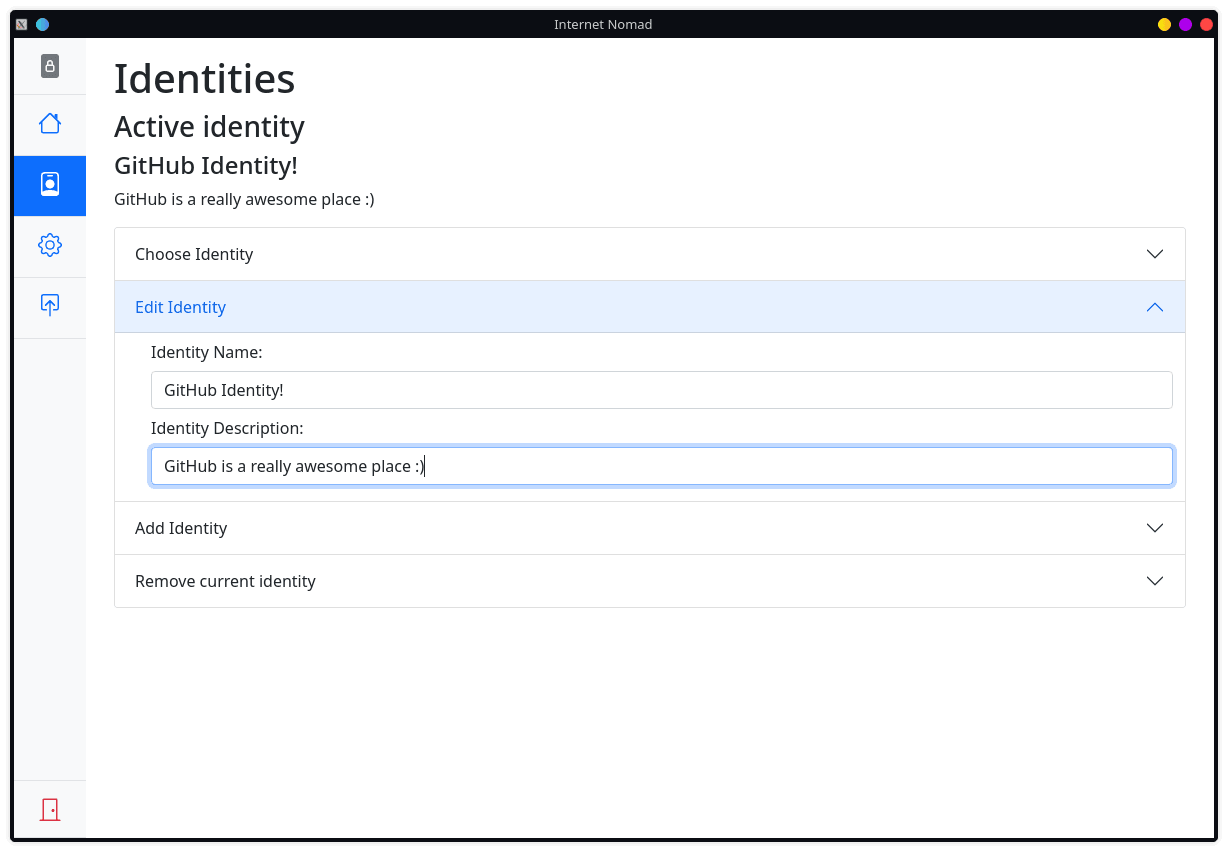
Another distinct feature of the password manager is that it implements “Identities”, which are fundamentally a collection of accounts. The password manager is designed as a supplement for operating on the Tor network. Having identities ensures that the user does not accidentally “link”, accounts that they do not want to be linked together, allowing the user to assume an identity per Tor session. This allows for a much safer operating security when doing sensitive tasks.
Accounts
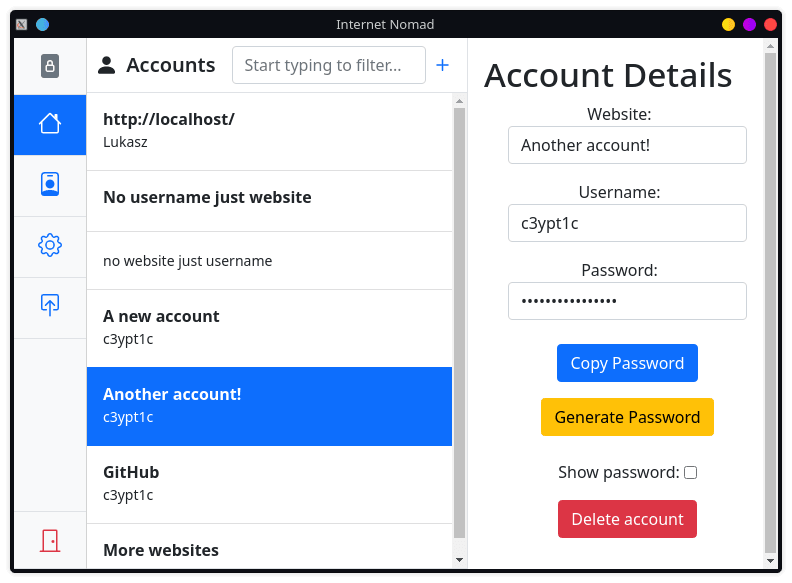
The password manager has many common password manager functions. It's possible to create accounts, generate passwords, delete and edit accounts and more.
Password Manager Report
This was mostly an exert from my Password Manager Report. The full project is available on GitHub, if you'd like to view it and play with it.
[^1]: Adi Shamir (1979) 'How to Share a Secret', Massachusetts Institute of Technology, 22(11), pp. 612-613. [^Blowfish]: Blowfish: https://en.wikipedia.org/wiki/Blowfish_(cipher) [^AES]: AES: https://en.wikipedia.org/wiki/Advanced_Encryption_Standard [^ENC]: ENC: https://en.wikipedia.org/wiki/Block_cipher_mode_of_operation [^PBKDF2]: PBKDF2: https://en.wikipedia.org/wiki/PBKDF2 [^Argon2]: Argon2: https://en.wikipedia.org/wiki/Argon2 [^KDF]: https://en.wikipedia.org/wiki/Key_derivation_function